OWASP Cryptographic Failure : Information Disclosure Vulnerabilities
- Quality Engineering
OWASP Cryptographic Failure : Information Disclosure Vulnerabilities
These Vulnerabilities allow you to access information that should not be attainable or visible.
What is information disclosure?
Information disclosure, also known as information leakage, is when a website unintentionally reveals sensitive information to its users. Depending on the context, websites may leak all kinds of information to a potential attacker, including:
- Data about other users, such as usernames or financial information
- Sensitive commercial or business data
- Technical details about the website and its infrastructure
Lets Practice :
a ) Discovering Database Login Credentials
Register on : https://portswigger.net/users/register
open the practice lab : https://portswigger.net/web-security/information-disclosure/exploiting/lab-infoleak-via-backup-files
– Take a minute to read Solution
Now click on Access the lab
Now add /robots.txt in url of target website.
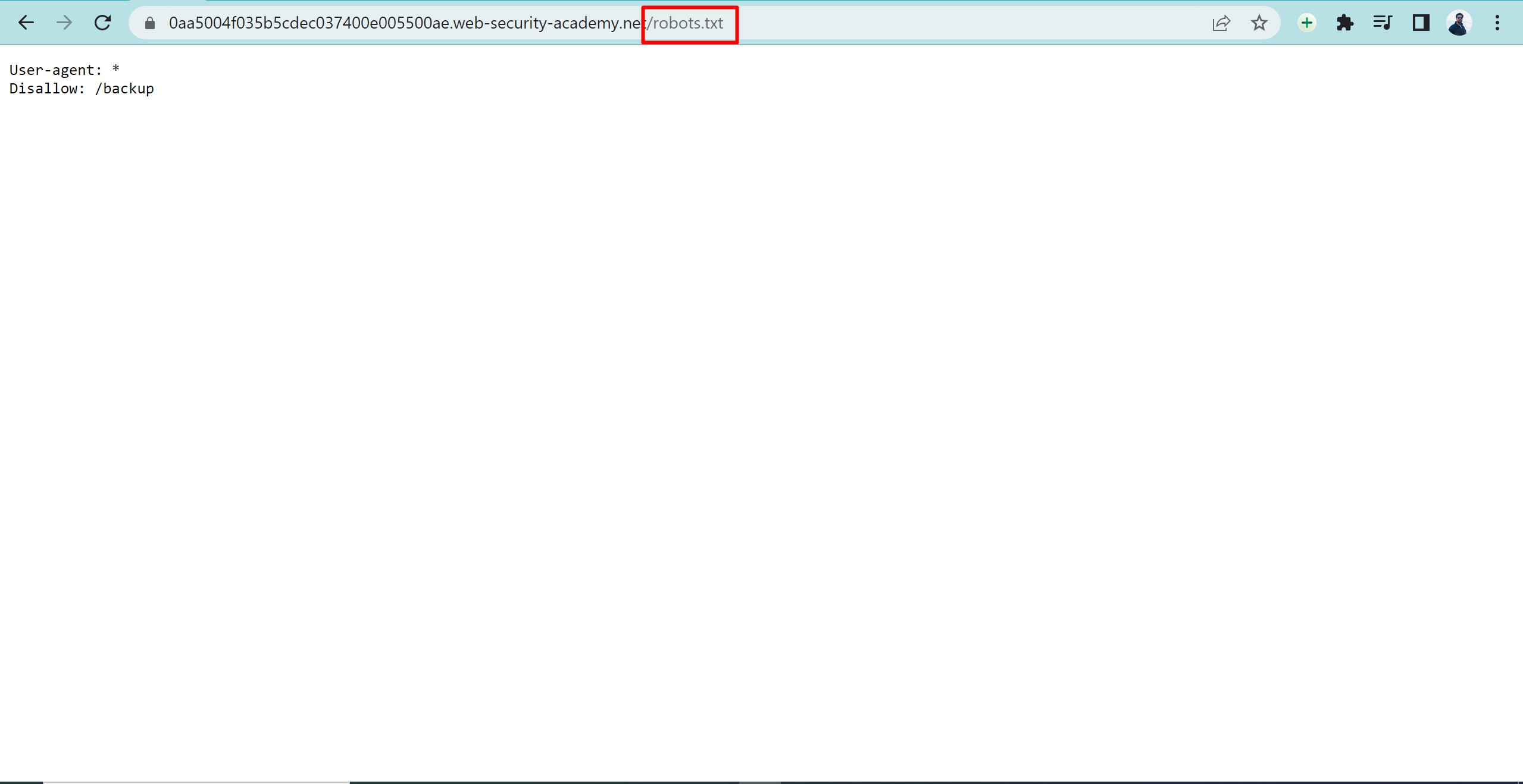
here we will see some files with allow and disallow attribute we can try open these files of target website to see whether if they are leaking some non attainable information or not.
Now open https://Targetwebsite/backup
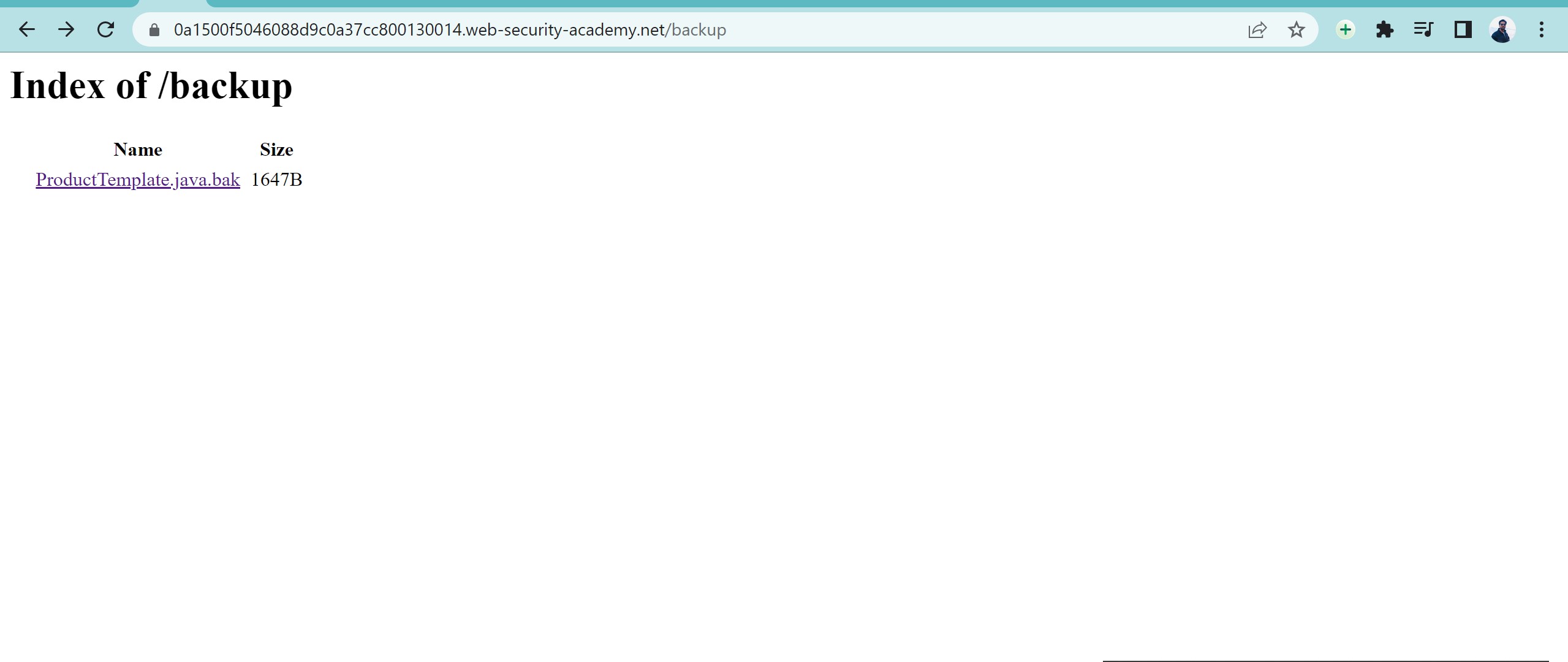
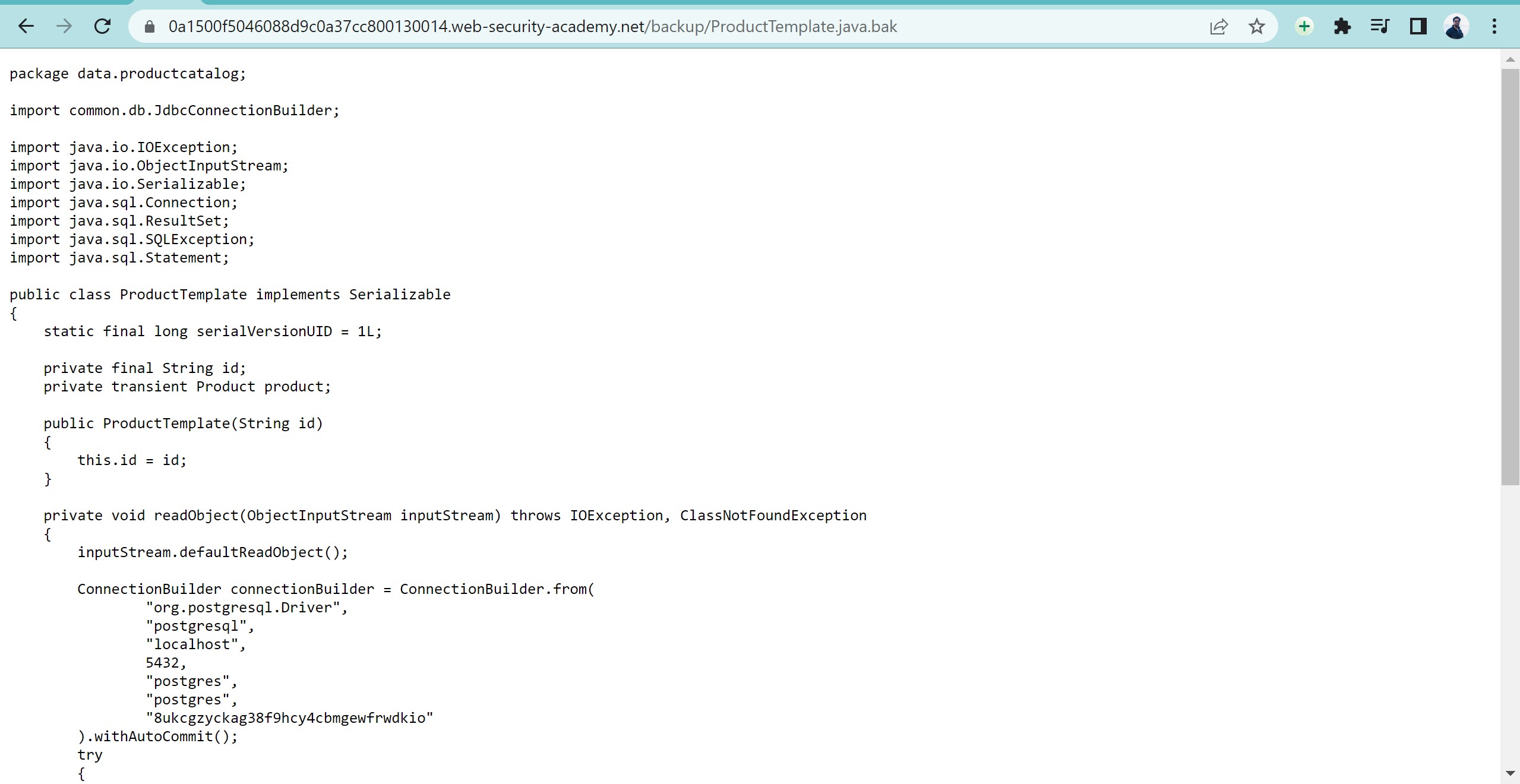
once you open this you can see the root directory is disclosing one java file when we click on it and open this we get entire source information and database connection details – which makes the website vulnerable.
b ) Discovering Endpoints & Sensitive Data with Feroxbuster
So, Now it may happen target website do not have robots.txt endpoint or it is not revealing any sensitive information directly. In such cases discovering each end point may time consuming . here we are going to use a tool “Feroxbuster” and it will be automatically discovering all the endpoints.
Reference : https://github.com/epi052/feroxbuster
Get common.txt file for wordlist : https://github.com/danielmiessler/SecLists/tree/master/Discovery/Web-Content
Practice Lab : https://portswigger.net/web-security/information-disclosure/exploiting/lab-infoleak-on-debug-page
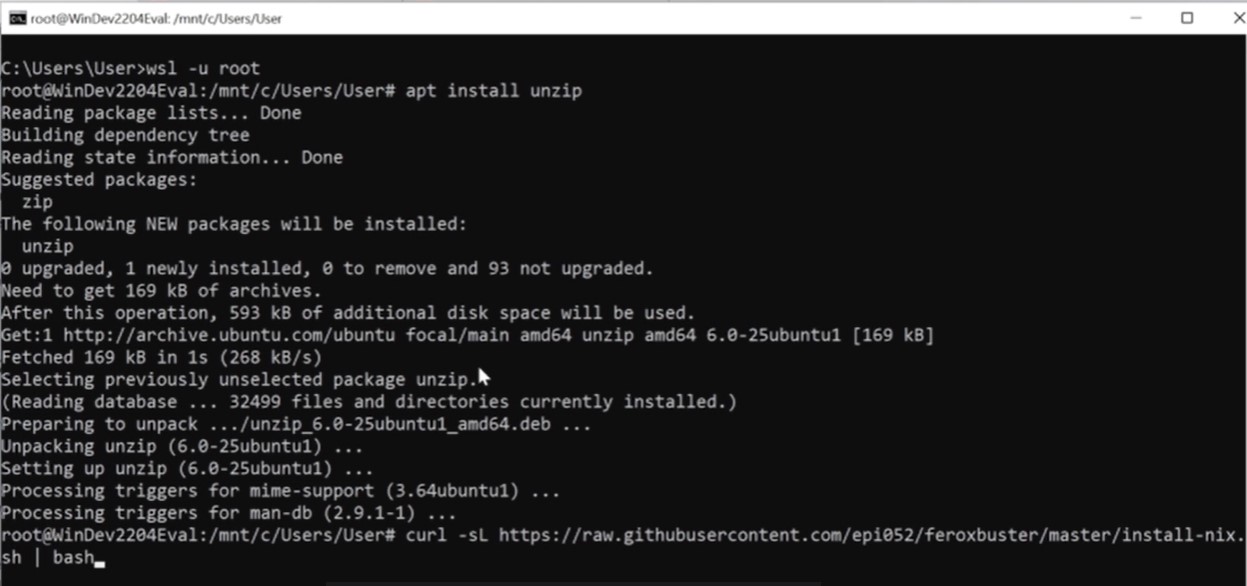
To install feroxbuster on Linux or MacOs : curl -sL https://raw.githubusercontent.com/epi052/feroxbuster/master/install-nix.sh | bash
To install feroxbuster on windows : install window subsystem for linux with command
- wsl –install
- wsl -u root
- apt install unzip
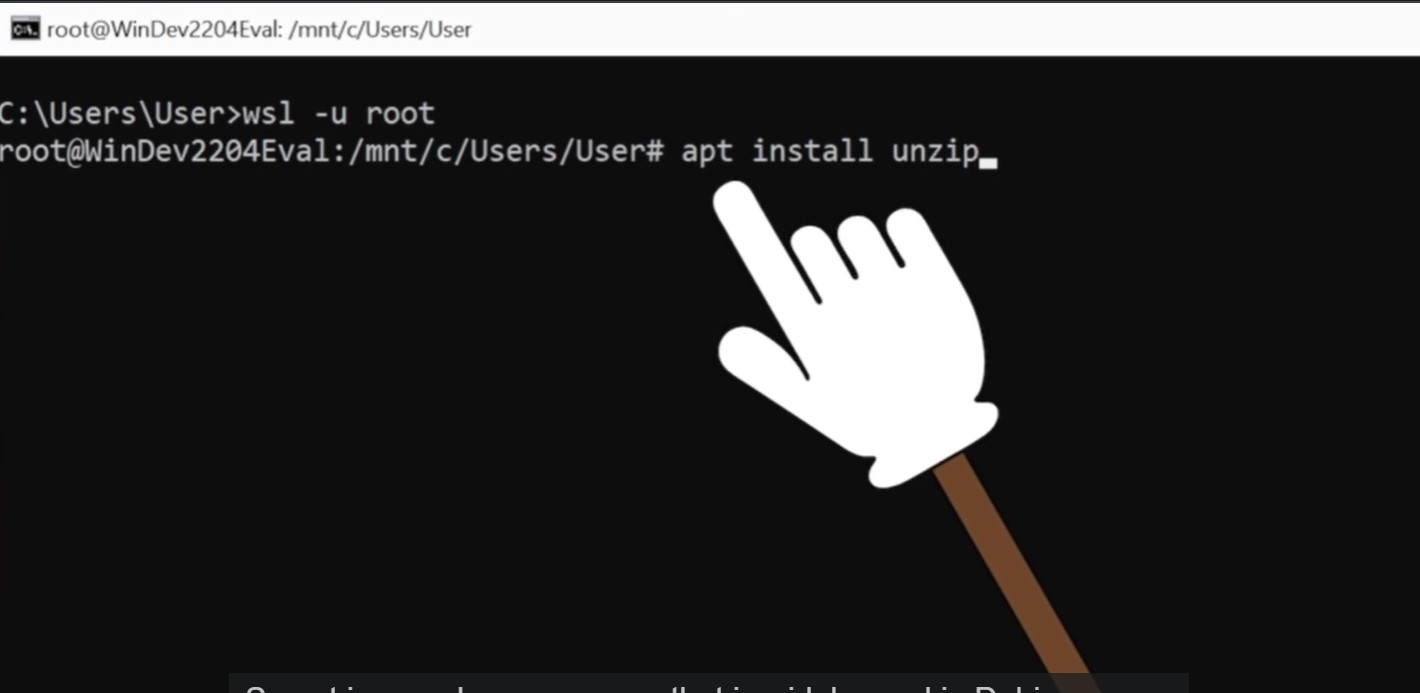
Now install feroxbuster with command : curl -sL https://raw.githubusercontent.com/epi052/feroxbuster/master/install-nix.sh | bash
Now give the command :
./feroxbuster -u https://0a1b007304d87795c092db6c00ee00f2.web-security-academy.net/ -w Downloads/common.txt
In above command -u stands for url and -w stands for wordlist and there is target url [ Get this url from practice lab ] following -u. and wordlist file [common.txt] is just predefined set of instruction which we are passing in text format.
lets run this and it will start discovering end points
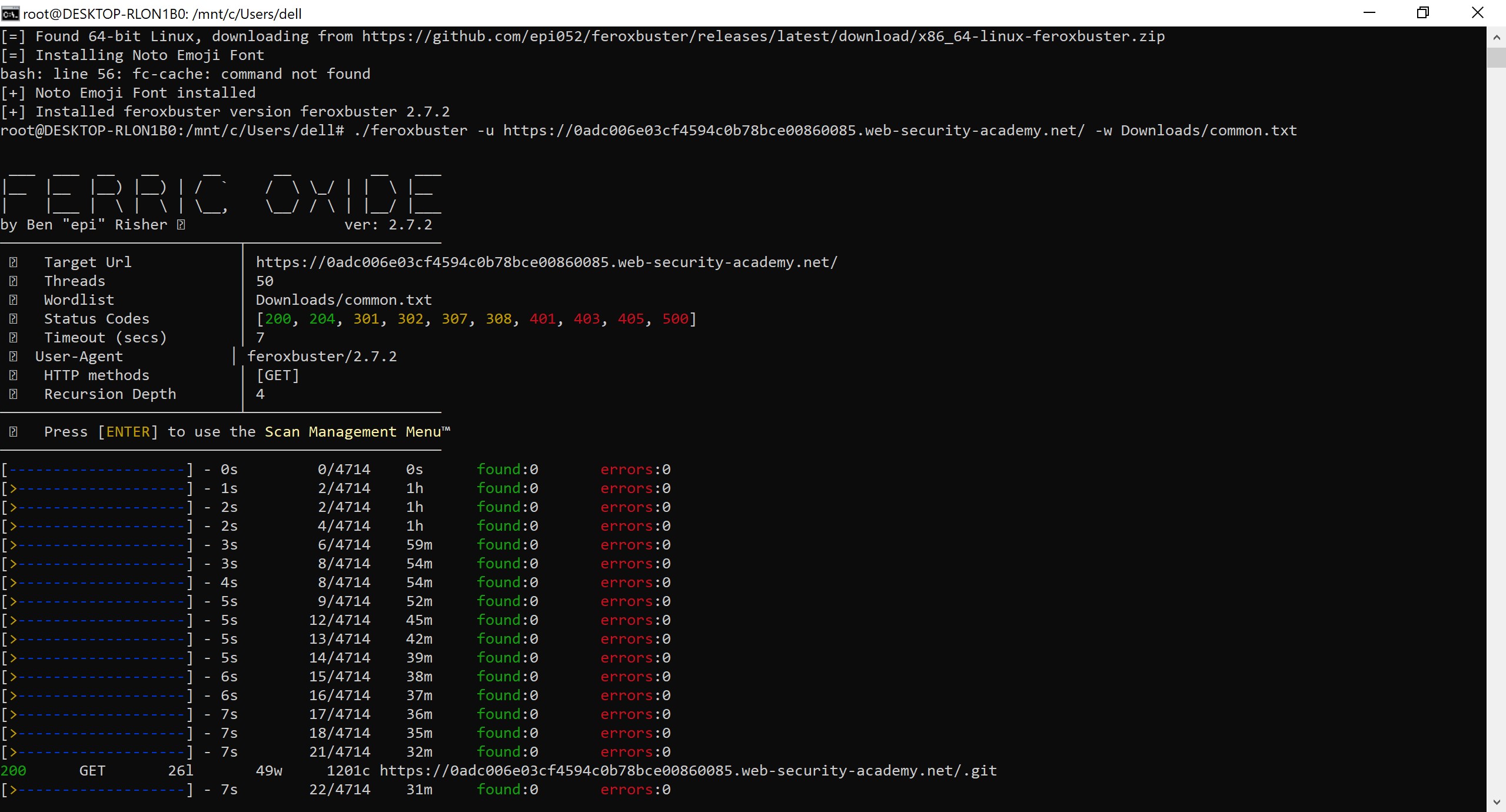
look carefully if there is any sensitive endpoint.
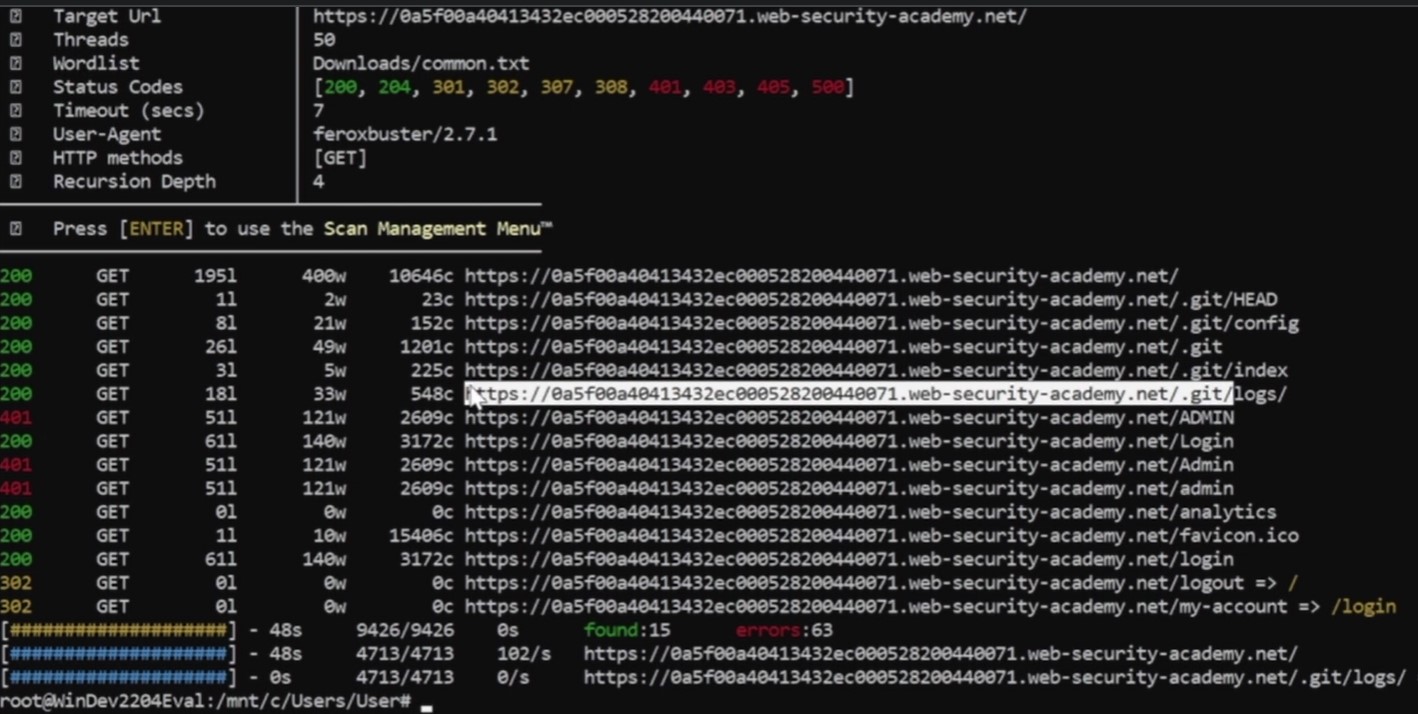
Get this url and open with browser, Here we can see all the sensitive information revealed also we can clone this repository and open with git to know the version history.
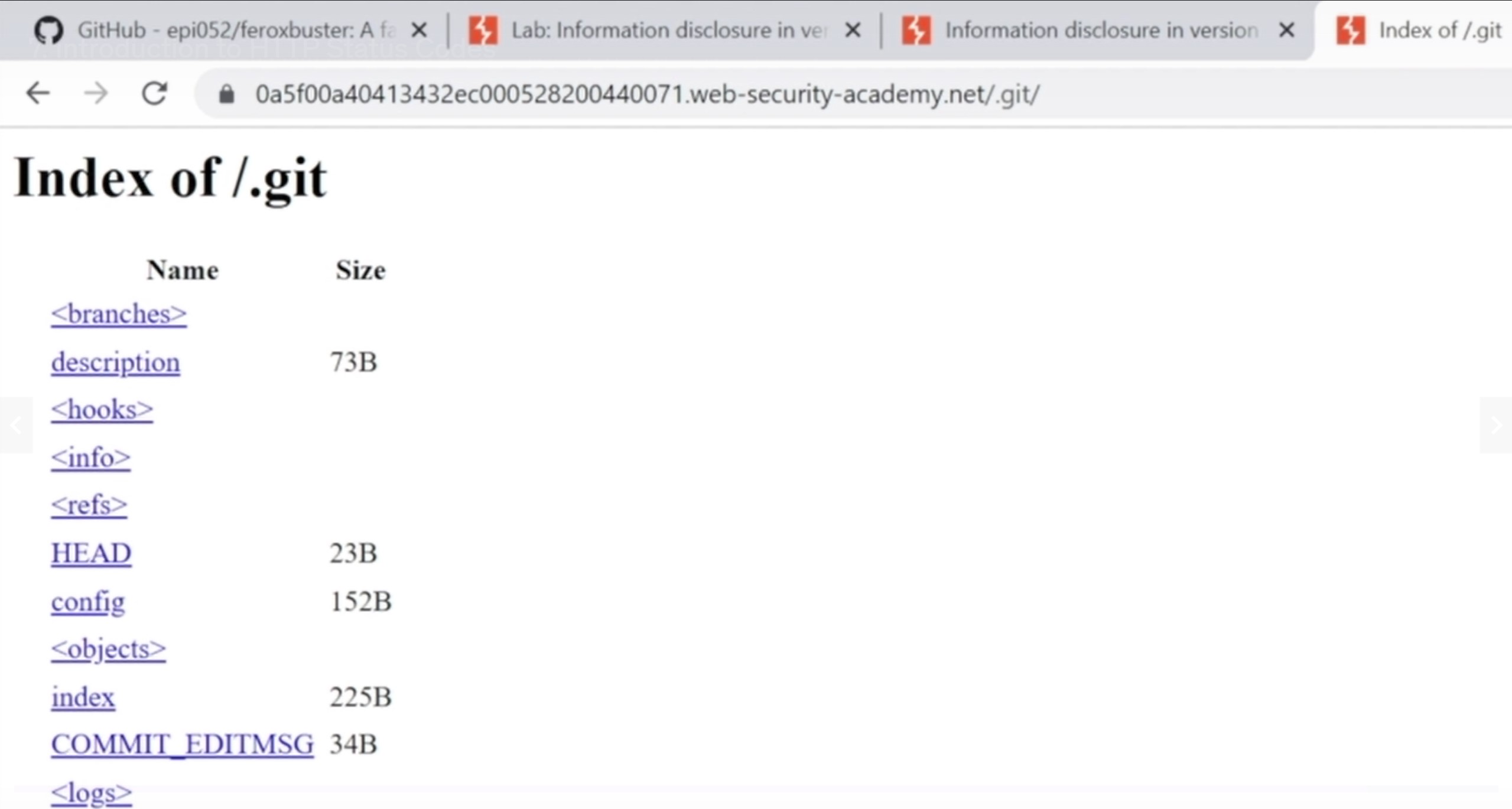
I hope you enjoyed this informative blog. Feel free to ask any questions or queries in comments or Join on linkedIn.