XML Signatures –Build a Secure Channel for data exchange and communication
- General
- Performance and Security
XML Signatures –Build a Secure Channel for data exchange and communication
Why the need of Signatures
When sending a message between two parties we need to address the problem that message should not be read or altered by any middle men. Solution is to encrypt the message and then sign it.
Digital Signature
Digital signature is “a value computed with a cryptographic algorithm and appended to a data object in such a way that any recipient of the data can use the signature to verify the data’s origin and integrity.
It is used to validate the authenticity and integrity of a message, software or digital document.
An XML signature is a digital signature only with several key properties. They are a standard for digital signatures in the XML data format, and they allow you to authenticate and protect the integrity of data in XML and web service transactions.
Oracle provides crypto package and has an excellent guide on generating XML signatures. It details out all possible attributes, methods for generating and validating the signatures.
https://www.oracle.com/technical-resources/articles/java/dig-signature-api.html
Challenges Faced during Signature verification
• Client’s X509 certificate which was shared to server was generated using SHA1RSA. instead of SHA256RSA as signature algorithm.
• Private key had to be 2048 bits.
• Both client & server must use same CanonicalizationMethod and Signature Method Algorithm else signature will not get validated.
Other tools/libs for XML signatures
• Chilkat – https://tools.chilkat.io/xmlDsigVerify.cshtml
• XML validator buddy
• Php Library – https://github.com/robrichards/xmlseclibs
Now let’s try to understand the Digital Signatures in detail –
Digital Signature Generation
1. The sender computes a message digest and then encrypts the digest using the sender’s private key, forming the digital signature. . (digital signature = encryption (private key of sender, message digest) and message digest = message digest algorithm(message)).
2. The sender transmits the digital signature with the message.
3. The receiver decrypts the digital signature using the sender’s public key, regenerating the sender’s message digest. .(This assures authenticity, as only sender has his private key so only sender can encrypt using his private key which can thus be decrypted by sender’s public key)
4. The receiver computes a message digest from the message data received and verifies that the two digests are the same.
If the digital signature is verified, the receiver knows that:
• The message has not been modified during transmission.
• The message was sent by the entity that claims to have sent it.
How I used XML signatures to secure communication bw client & server
• Create public-private key pair
• Generate csr , share with CA to get my trusted certificate
• Share certificate with server
• Create request payload in xml , signs it using my private key, attach my X509 certificate (received from CA) in the message and send it.
• Server will verify the signature and then process the request.
• Server will prepare response XML , signs the message using server’ s private key and sends it back to client along with server’s public certificate.
•Client will verify the signature and process the response.
Self Signed Certificates
https://blogg.bekk.no/how-to-sign-a-certificate-request-with-openssl-e046c933d3ae
https://gist.github.com/fntlnz/cf14feb5a46b2eda428e000157447309
Useful Commands
Generate Private Key –
|
1 |
openssl genrsa -out <privatekey.pem> 2048 |
Generate Public Key –
|
1 |
openssl rsa -in <privatekey.pem> -pubout -out <publickey.pem> |
Generate CSR –
|
1 |
openssl req -new -key <privatekey.pem> -out req.csr |
Generate Public X509 Certificate –
|
1 |
openssl req -x509 -sha256 -new -key <privatekey.pem> -days 3650 -out <publickey.crt> |
Generate p12 file –
|
1 |
openssl pkcs12 -export -out naagkeystore1.p12 -inkey <privatekey.pem> -in <publickey.crt> |
Read about Mutual SSl – https://dzone.com/articles/securing-rest-apis-with-client-certificates
Read how to attach certificate while sending the curl Request – https://stackoverflow.com/questions/36131857/ssl-certificate-with-php-curl
Where Digital Signatures are used
• Digital Certificates(X509) – used to prove your identity that you are actually who you are telling. It has your public key signed by a trusted 3rd party(certificate issuing authority) ‘s private key. You can also self sign the certificate but then it will not be a trusted certificate. Now when someone wants your public keys, you send them the certificate (instead of sharing the public key) , they verify the signature on the certificate, and if it verifies, then they can trust your keys. So Digital certificate has your public key and digital signature of certificate issuing authority. Read below for Digital Certificate Generation.
• SSL-TLS – During SSL handshake server sends it’s digital certificate to client. Client can use this certificate to ensure that identity of server. Read more here
• Aadhar offline ekyc – Read below
Digital Certificate Generation
• Generate a private-public key pair.
• Create a CSR (certificate signing request) and share with Certificate Authority (CA)
• CA signs the CSR using CA’s private key and attach its Digital Signature. ???
How it looks like –
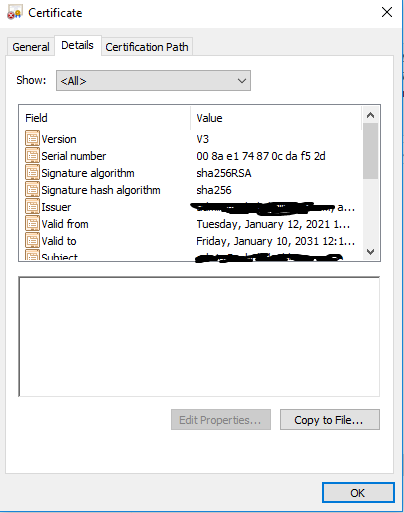
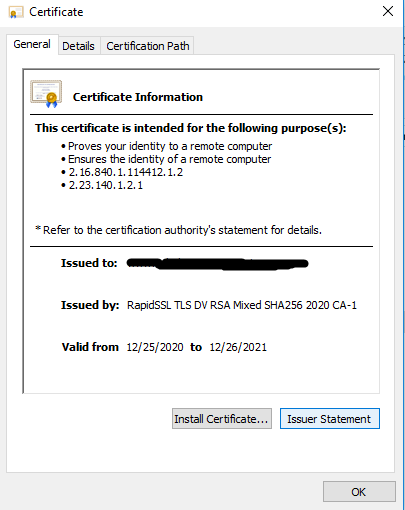
Aadhar offline kyc process
Few weeks back when I was going through the Adhar offline ekyc process, I came to kow that Aadhar also uses XML digital signatures to share the data to agencies for KYC purpose.
Aadhar ekyc process makes you download a XML file which is zipped and password protected. The data present in the XML is also digitally signed. This XML file contains user private information like –
• Resident Name
• Download Reference Number
• Address
• Photo
• Gender
• DoB/YoB
• Mobile Number (in hashed form)
• Email (in hashed form)
Aadhaar Paperless Offline e-KYC data is encrypted using a “Share Phrase” provided by the Aadhaar number holder at the time of downloading which is required to be shared with agencies to read KYC data.
https://uidai.gov.in/ecosystem/authentication-devices-documents/about-aadhaar-paperless-offline-e-kyc.html
Steps to generate Aadhar Paperless Offline ekyc – https://enps.kfintech.com/AadharZipDoquments/Offline-Aadhaar-eKYC-process.pdf
Lets see how a signed XML looks like.
Sample signed XML for Aadhar eKYC-
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
<OfflinePaperlessKyc referenceId=""> <UidData> <Poi dob="" gender="" name="" e="" m=""/> <Poa careof="" country="" dist="" house="" loc="" pc="" po="" state="" street="" subdist="" vtc="" /> <Pht></Pht> </UidData> <Signature xmlns="http://www.w3.org/2000/09/xmldsig#"> <SignedInfo> <CanonicalizationMethod Algorithm="http://www.w3.org/TR/2001/REC-xml-c14n-20010315" /> <SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" /> <Reference URI=""> <Transforms> <Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" /> </Transforms> <DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" /> <DigestValue></DigestValue> </Reference> </SignedInfo> <SignatureValue></SignatureValue> <KeyInfo> </KeyInfo> </Signature> </OfflinePaperlessKyc> |
References –
1. https://ikriv.com/blog/?p=1827
2. IBm Support Knowledge Center
3. Oracle Technical Resources – https://www.oracle.com/technical-resources/articles/java/dig-signature-api.html
4. p12 export command hangs while using openssl on windows – Use winpty before openssl. https://stackoverflow.com/questions/34156938/openssl-hangs-during-pkcs12-export-with-loading-screen-into-random-state